Mid-Term Exam
Computer Networks
NCNU CSIE
Date: November 13th, 2008
Time: 15:10-18:00
- (10%) If a LEO satellite is exactly 1,500 km above the earth's
surface, how long does it take a radio signal to reach the satellite
and be transmitted back? (Assume the signal propagates at the speed
of light, i.e., 300,000 km per second, and that the satellite takes 53
microseconds to retransmit a signal.)
- (10%) When using even parity, what is the parity bit for the character
'N', whose ASCII code is 78?
- (10%) Explain why "hidden nodes" will cause a problem for the
collision detection. How does IEEE 802.11 solve this problem?
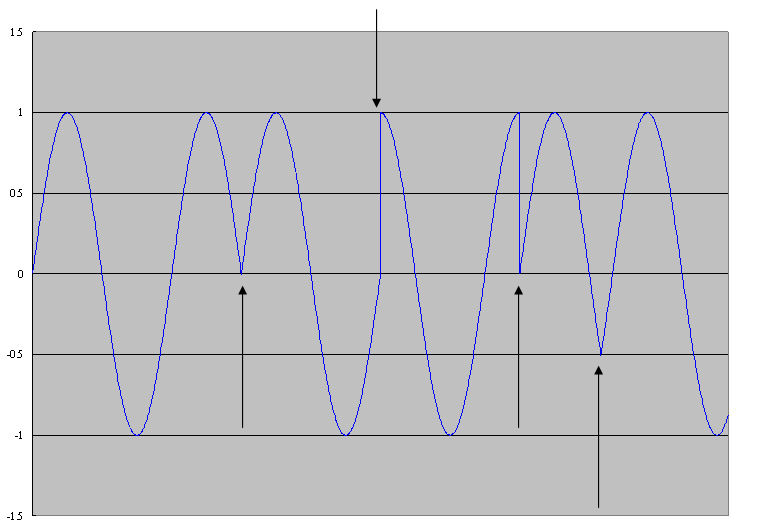
- (10%) Consider the following figure which shows the wave that
results from phase shift modulation (PSM). Suppose a sine wave
completes a cycle in 2Łk radians, what are the values of the 4 shifts
indicated by the arrows?
- (10%) Explain the purpose of the following commands on Unix:
- ls
- pwd
- less
- grep
- gcc
- (20%) Consider the following source code (/usr/src/usr.bin/cksum/sum2.c)
which shows the algorithm to compute the cksum of a file on UNIX.
uint32_t cksum;
int
nr;
u_char *p;
u_char buf[8192];
/*
* Draft 8 POSIX 1003.2:
*
* s = sum of all bytes
* r = s % 2^16 + (s % 2^32) / 2^16
* cksum = (r % 2^16) + r / 2^16
*/
cksum = 0;
while ((nr = read(fd, buf, sizeof(buf))) > 0)
for (p = buf; nr--; ++p)
cksum += *p;
if (nr < 0)
return (1);
cksum = (cksum & 0xffff) + (cksum >> 16);
cksum = (cksum & 0xffff) + (cksum >> 16);
Note that this algorithm compute the summation of every character as an
8-bit integer (instead of every pair of characters as a 16-bit integer
shown in Figure 7.6 in the textbook). Apply this algorithm to a
file containing the following string
N
|
C
|
N
|
U
|
\n
|
4E
|
43
|
4E
|
55
|
0A
|
and predict the final checksum.
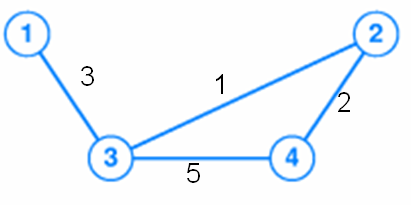
- (20%) Consider a network topology illustrated by the following
weighted graph.
Run the distance-vector algorithm step by step, to build the routing
table on each node.
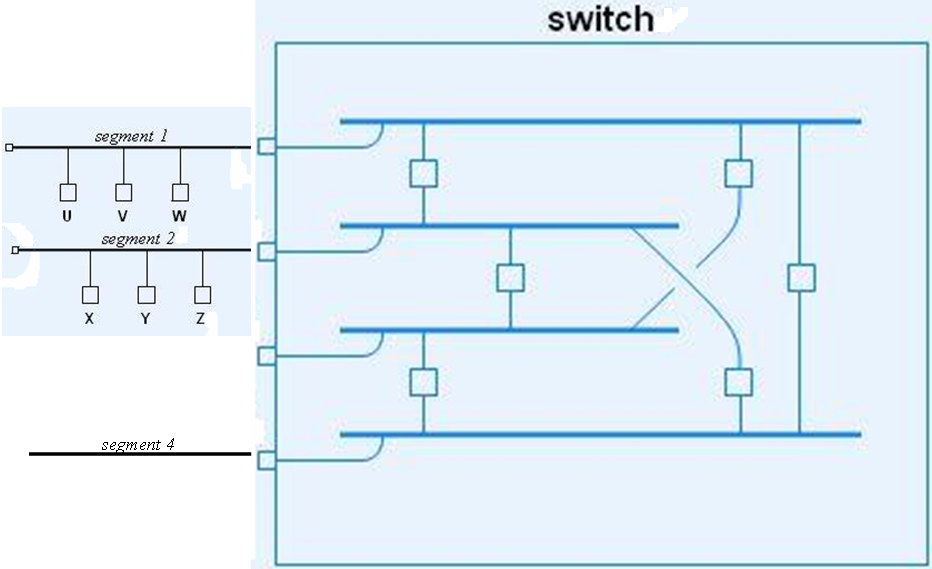
- (20%) Consider an Ethernet switch shown in the following figure,
where each pair of segments is interconnected by a (internal) bridge.
Suppose after the switch boots, the following events try to transmit
Ethernet frames:
- U sends to V
- V sends to U
- Z broadcasts
- Y sends to V
- Y sends to X
- X sends to W
- W sends to Z
What frames will be transmitted to segment 4? Illustrate how you derive
this answer by showing the learning process of the bridges.