Final Exam
Computer Networks
NCNU CSIE
Date: January 14th, 2009
Time: 15:10-18:00
A. True or False
- Suppose the PING command reports that the round-trip delay
between Taipei and New York is 250ms, and the communication path is
symmetric. If radio transmissions
propagate at the speed of light, will it be possible that the ICMP
request and reply were transmitted through a GEO satellite?
- Consider the above question while assuming that your computer
connects to the Internet via a broadcast satellite system, whose uplink
is a landline optical fiber. Suppose in an optical fiber, data can be
transmitted at 70% of the speed of light,. If the length of the optical
fiber between Taipei and New
York is 21,000km, and the altitude of the LEO
satellite is 6000km, can we expect the
round-trip time to be shorter than 110ms?
- Consider the following source code (/usr/src/usr.bin/cksum/sum2.c)
which shows the algorithm to compute the cksum of a file on UNIX.
uint32_t cksum;
int
nr;
u_char *p;
u_char buf[8192];
/*
* Draft 8 POSIX 1003.2:
*
* s = sum of all bytes
* r = s % 2^16 + (s % 2^32) / 2^16
* cksum = (r % 2^16) + r / 2^16
*/
cksum = 0;
while ((nr = read(fd, buf, sizeof(buf))) > 0)
for (p = buf; nr--; ++p)
cksum += *p;
if (nr < 0)
return (1);
cksum = (cksum & 0xffff) + (cksum >> 16);
cksum = (cksum & 0xffff) + (cksum >> 16);
Note that this algorithm compute the summation of every character as an
8-bit integer (instead of every pair of characters as a 16-bit integer
shown in Figure 7.6 in the textbook). Apply this algorithm to a
file containing the following string
P
|
A
|
S
|
S
|
\n
|
50
|
41
|
53
|
53
|
0A
|
Will the final checksum be 197?
- Broadcasting is extremely inefficient, because the packets will
interrupt the CPU and ask the operating system to determine whether the
frame should be ignored.
- Multicast does not solve the above problem, because CPU also needs
to
investigate all the frames received by the network interface card.
- IP is a reliable protocol which can be utilized by applications
to transmit data to remote computers.
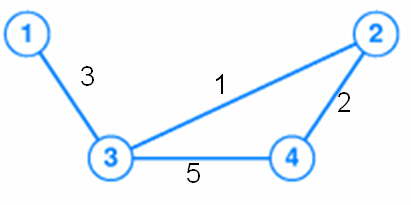
- Consider a network topology illustrated by the following
weighted graph.
If we run the distance-vector algorithm step by step, and build the
routing
table on each node, we shall see that the shortest distance from node 3
to node 4 would be 5.
- Consider a TCP segment from the sender Alice.
If in its IP header,
- H.LEN=01012 (which means 20
Bytes),
- TOTAL LENGTH = 05DE16 (which
means 1500 Bytes),
in its TCP header,
- SEQUNCE NUMBER = 8951ABFB16
(=2032207310),
- HLEN=816 (which means 32 Bytes)
We can predict that the sequence number of the next TCP segment should
be 20323521.
B. Choose the right answer
- Which command can be used to show the intermediate routers along
the path to a remote destination?
- ping
- showroute
- tracert
- ls
- For the "CNAIapi" provided in our textbook, how does the "recv()"
function signify that end-of-file has been reached?
- By returning a NULL pointer.
- By calling the recv_eof() function.
- By returning an integer value -1.
- By returning an integer value 0.
- Which organization defined the standard RS-232?
- ITU
- IEEE
- IETF
- EIA
- In RS-232, a start bit is represented by
- +15V
- +5V
- +3.3V
- 0V
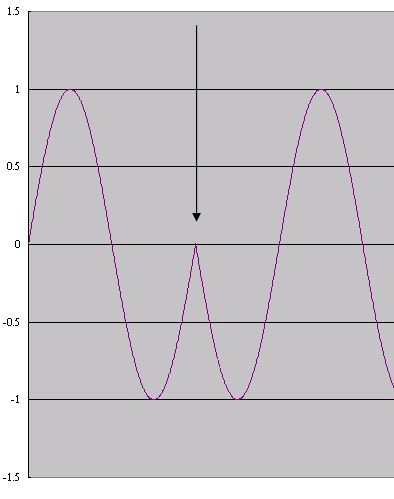
- Consider the following figure which shows the wave that results
from phase shift modulation (PSM). Suppose a sine wave completes
a cycle in 2Łk radians, what is the value of the shift
indicated by the arrow?
- Łk/3
- Łk/2
- Łk
- 3Łk/4
- Which of the following media does not suffer from
electromagnetic interference?
- Copper wire
- Glass fiber
- Radio
- Microwave
- What is the maximum length of an RS-232 cable?
- 10m
- 15m
- 50m
- 100m
- Which broadband technology uses multiple frequencies to achieve
higher throughput?
- TDM
- FDM
- DWDM
- 1 and 2
- 2 and 3
- Suppose we have 10 nodes. If we want to have
point-to-point connections between every pair of nodes, what is the
totaly number of connections?
- 10
- 9
- 45
- 55
- Which of the following is a LAN topology?
- Star
- Ring
- Bus
- All the above
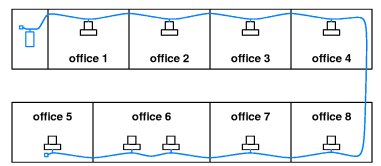
- 1The Etherenet wiring scheme shown in the following figure is
_________.
- 10Base2
- 10Base5
- 10BaseT
- What is the length of an Ethernet address?
- 4 bytes
- 6 bytes
- 14 bytes
- 20 bytes
- NCNU has 34 class C networks. Therefore, excluding the IP
addresses which represent the network ID and the broadcast address, how
many IP addresses can we assign to hosts?
- 8192
- 8704
- 8128
- 8636
- Before an ARP frame can be transmitted over the network, it must
be encapsulated in a
- TCP header
- UDP header
- IP header
- Ethernet header
- Generally fragmentation will occur when datagrams pass networks
- From a WAN to a LAN
- From a LAN to a WAN
- From both directions
- None of the above
- The ICMP protocol is tranported over
- TCP
- IP
- UDP
- ARP
- What is the theoretically maximum size of an IP header?
- 20 bytes
- 40 bytes
- 60 bytes
- 80 bytes


